Top 21 Linux Interview Questions
Linux offers security, scalability and easy configurations for administrators to manage the systems more efficiently.
Linux interview questions for freshers are helpful for students aspiring to become Linux administrators.
- 4.9 Rating
- 24 Question(s)
- 60 Mins of Read
- 895 Reader(s)
Linux is a free Open-source operating system.
UNIX is a proprietary operating system used by Bell laboratories. LINUX is an open-source operating system and is a non-proprietary operating system.
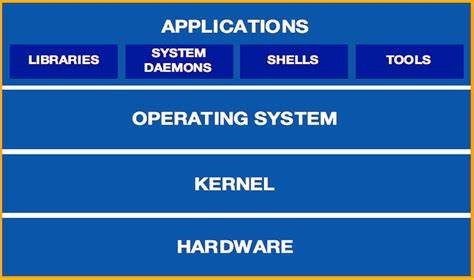
It is a low-level system software that allows users to manage system resources and an interface for use-interaction.
LILO stands for Linux Loader. It loads the Linux operating system into the main memory to start execution. The BIOS conducts some initial tests and transfers the control to the Master Boot Record. Linux OS is then loaded by LILO and started. LILO allows faster booting of Linux.
The basic components of Linux include:
- Kernel: It is the core component of Linux used to manage the operations and hardware.
- Shell: It is the Linux interpreter used to execute commands.
- Graphical User Interface: GUI is another way for the user to interact with the system.
- System Utilities: These include the software programs used to manage the system.
- Application Programs: These include a set of functions or programs designed to accomplish a specific task.
Naming convention: DOS files must have an 8-character filename followed by a dot and an extension with three characters. There is no naming convention for BASH files.
Case sensitive: DOS commands are not case sensitive whereas the BASH files are case-sensitive.
/ and \ commands: In DOS / command is used as an argument delimiter and \ is used as a directory separator. / command in BASH is used as directory separator and \ acts as escape character.
Symbolic links are shortcuts that provide instant access to the object they are pointing. There is no need for giving the entire path of the directory, file, or program in Linux.
Read, Write and Execute are the three types of permissions allowed in Linux.
Read: Allows users to read the files in a directory
Write: Allows users to write to the file or add new files to the directory
Execute: Allows users to look up for a specific file within a directory or run the file
The command used to grant permission is specified with r for read, w for write, and x for execute.
Virtual desktop feature in Linux allows users to shuffle between desktops having different program windows. For accessing a virtual desktop click on the upper left corner of the program window and click on the pushpin-like icon. It will allow the application to be accessed across various virtual desktops.
he root account refers to the system administrators account in Linux.
The five main directory command in Linux are:
- pwd: Displays the path of the current working directory
- Is: Lists all the files and directories of the current directory
- cd: Used to change the current directory
- mkdir: Used to create a new directory
- rmdir: deletes the specified directory
Vi editor consists of three modes that include:
Regular/Command mode: Allows to view the content
Insertion/edit mode: Allows to insert or delete content
Replacement mode: Allows to overwrite content
The process management system calls include:
- fork (): Used to create a new process
- exec (): Execute a new program
- wait ():Wait until the process completes its execution
- exit (): Exit from the process
To obtain the Process ID, the following System Calls are used:
- getpid (): get the unique process id of the process
- getppid (): get the parent process unique id
Regular Expressions help search for data having a particular pattern. The commands used with Regular Patterns are tr, sed, vi and grep.
The common symbols used in Regular Expressions are:
. Match any character
^ Match the beginning of the String
$ Match the end of the String
* Match zero or more characters
Represents special characters
? Match exactly one character
Linux installation requires two partitions.
The first partition is the local file system where all the files of the OS, files of applications and services, and files of the user are stored. The second partition acts as Swap Space that is an extended memory for RAM.
The commands to schedule tasks in Linux include cron and at.
Cron commands schedule recurring tasks at specific times. Cron commands execute the tasks stored in the cron file. The cron command reads the string from this file and schedules the task.
The export command sets and reloads the environment variables. For example, if you want to set the Java path, then the command would be:
$ export JAVA_HOME = /home/user/Java/bin
Daemons are services running in the background and helpful in extending the functionality of the operating system. They offer several functions that might not be available in the operating system.
A daemon’s main task is to listen to a service request and act upon it at the very same. The daemon is disconnected after finishing a task and it waits for further requests
The /usr/local directory contains the locally installed files. The directory plays a vital role when files are stored on some network. Moreover, it stores software packages installed from a source or software not officially accompanying the distribution.
You need to use the NOHUP command first. It will stop the process receiving the NOHUP signal. The termination will log you out of the program that was invoked. Then start the Linux server, and enter the name of the Linux program followed by the & symbol to run the process in the background.
The various types of instances in AWS include
General purpose instance: The general purpose instances are used in development environments, build servers, code repositories, low traffic websites and web applications, and micro-services.
Compute optimized instance: These type of instance consist of C3 and C4 instances that are mainly used by applications that require high CPU usage.
GPU instances: These instances are used for gaming applications that require heavy graphics and 3D application data streaming.
Memory optimized instances: These instances are designed for memory-intensive applications that consists of R3 instances.
Storage optimized instances: These instances are of two types I2 and D2.
I2 provides the heavy SSD necessary for sequential read, and write access to a large data set. It is preferred for online transactions, relational databases, Cache for in-memory databases, Data warehousing applications and Low latency Ad-Tech serving applications.
D2 instance consists of a high-frequency Intel Xeon E5-2676v3 processor, HDD storage, and High disk throughput.
Stopping shuts down the instance. The corresponding EBS volume is still attached to the EC2 instance allowing it to restart.
Terminating: It removes the instance permanently from the AWS account. The corresponding EBS is removed and does not allow to restart the EC2.
VPC stands for Virtual Private Cloud. It allows to customise the networking configuration. It is a network that is logically isolated from another network in the cloud. It allows to have IP address range, internet gateways, subnet, and security groups.
Recorded Videos
- Enhance students learning Experience.
- Relief the pressure of Note-Taking.
- Lifetime Access.
- Learning Flexibility.
- Easy to retakes of each sessions.
- Pocket friendly course.
Live Interactive Classes
- Lectures bring together diversed group of students to learn in different ways.
- Live interactive Instructor-led training.
- 24 x 7 hours learning assistance.
- Have a team of well-qualified expert trainers.
- Lifetime access of class recordings.
- Affordable fees.
Sign in to your account
Sign in to your account
Welcome back! Login with your data that you entered during registration.
-
-
Email and Password are case sensitive...
- Forget Password
Forget Password
We will send a password reset link on your email.
-
Please enter registered email.
Create Account
Create Account
Use your email for registration.
-
Please enter name
-
Please enter email
-
Please enter password
Must be grater 6 characters as long.
Can contain any letters a to z or A to Z.
Can contain some special characters eg(@,#,$,%,&,*,%).
Can contain any numbers from 0 to 9.